4 Steps to Mature Your Access Governance with AI and Agentic AI
Learn how AI and agentic AI are transforming Identity Governance and Administration (IGA) from manual workflows to autonomous decision-making – with real-world strategies and insights.

In this article
AI in Identity is having a moment. The era where Identity Governance and Administration (IGA) systems relied on building static role architectures, manually reconciling entitlements, tracking across spreadsheets and chasing down approvals is coming to an end. Modern vendors are climbing the AI maturity ladder - moving from static management to autonomous decision-making.
At Lumos, we call this shift what it truly is: the rise of Autonomous Identity. It is no longer a distant future, it is here today. Organizations can take the right next steps to drive down security risks, boost productivity and unlock cost savings across their access governance programs with the power of AI.
Here are four concrete steps to leverage AI and agentic AI for your access administration and governance.
- Establish your Data Foundation
- Assess the AI and Analytics Maturity Ladder
- Put Agentic AI to Work - Safely
- Close the Loop - from Insight to Remediation
Let’s walk through each of these key steps.
Step 1: Establish Your Data Foundation
AI can’t reason with what it can’t see. That’s why the first step to effective AI-driven access governance is visibility – into people, permissions, entitlements, usage, and behavior. For this, a large volume of contextual data needs to be available across different environments and systems to derive value from AI-powered systems.
Do this:
- Aggregate entitlements, roles, and access events across all critical systems; especially SaaS.
- Normalize and contextualize access (who has what, why, and how it's used).
- Identify key data gaps, such as: missing joiner/mover/leaver events, stale roles, or unmanaged apps, orphaned accounts, etc.
Key Takeaway: AI intelligence is no better than human intelligence when it comes to missing data. A strong identity data layer is non-negotiable and fundamental. Improve data management and work with IGA vendors to strengthen your AI-powered access administration.
Step 2: Assess the Analytics and AI Maturity Ladder
AI in IGA isn’t all-or-nothing. It’s a progression – from awareness to action. To cut through the vendor noise, it is helpful to understand the framework for measuring the AI maturity and their potential to achieve autonomy:
- Level 1: Descriptive
- Level 2: Diagnostic
- Level 3: Predictive
- Level 4: Prescriptive
Level 1: Descriptive - “What access exists / What is the current state?”
Show basic reports and dashboards outlining apps and identities, current access levels and status. This is the foundation for all higher levels.
- "List all users with the 'Admin' role in Snowflake."
- "Show all active accounts in Salesforce."
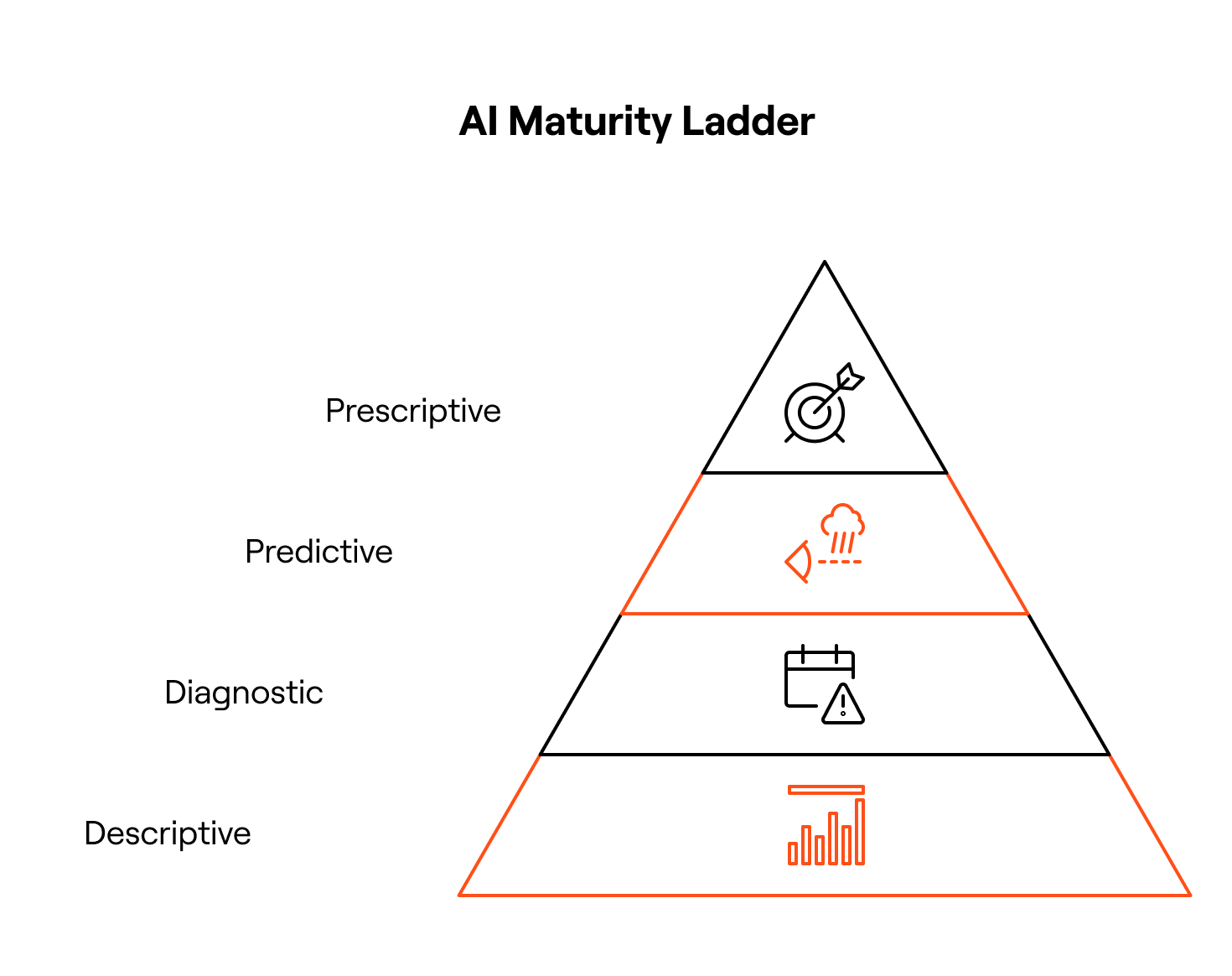
Level 2: Diagnostic - “Why did it happen / What looks risky / anomalous?”
Identify anomalies and deviations from policy, historical norms, or peer groups by correlating data points; flagging potential risks and suggesting root causes.
- "Flag dormant admin accounts based on zero usage in 90 days."
- "Identify users with outlier access compared to their defined role or team peers."
- "Detect conflicting entitlements violating a defined SoD policy."
Level 3: Predictive - “What might happen next / What is the likely risk?”
Use historical data, patterns, and ML/ AI models to forecast potential future risks, access needs, or the likelihood of certain events.
- "Predict a high probability of privilege creep for users moving into specific management roles based on historical peer group access accumulation."
- "Score the risk level of a pending access request based on user behavior, requested privilege sensitivity, and peer group analysis."
Level 4: Prescriptive - “What should be done / What can be automated?”
Recommend specific, optimized actions, remediation workflows and optimizations based on predictive analysis and defined policies.
- "Automatically revoking unused elevated privileges after 60 days and recommending time-based JIT access as an alternative."
- "Suggesting optimized, least-privilege role definitions based on analyzing actual entitlement usage patterns across similar users (AI Role Mining)."
- "Auto-approving low-risk access requests that perfectly match pre-defined, approved policies without human intervention."
Each step on this ladder builds the foundation for the next and to climb each rung, you need to evaluate where you are today and deliberately progress upward to mature your access governance with AI.
Do this:
- Map your current tools to this ladder. Most platforms don’t move beyond Levels 1–2.
- Identify quick wins at higher levels; like dormant privilege detection or AI-powered role and policy suggestions.
- Push vendors to show how insights move beyond dashboards into actions – in the product.
Key Takeaway: Build towards prescriptive automation—where AI insights drive secure, policy-bound outcomes. Work with your IGA vendor to assess how far up this ladder does their platform actually operate across different functions like access reviews, requests, policy creation. How transparent, explainable, and configurable are the AI/ML models?
Step 3: Put Agentic AI to Work—Safely
Agentic AI goes beyond analytics. These are AI-powered agents that can act: initiate a review, revoke risky access, or recommend policy updates in real time.
But with great power comes…governance. You need identity for the AI itself.
Do this:
- Define where you’re ready for agents to take action (e.g., revoking dormant admin access, auto-approving low-risk requests).
- Set clear boundaries: When should a human review be required? What policies must be enforced?
- Audit every agentic action – transparently and traceably.
Key Takeaway: Think of agentic AI as your identity co-pilot. It helps you scale security and productivity, without losing control. Lack of access standards means that analyzing the accuracy of role mining might still require human oversight, especially for business critical applications. Highly risk- and compliance-sensitive organizations may never get close to 100% comfort level with AI-recommended access policies and decisions.
Step 4: Close the Loop—From Insight to Remediation
The real test of AI maturity comes from whether it can actually update access. Whether it can act with the right signals and context, without disrupting business or productivity.
Descriptive analytics is helpful in streamlining operations. But closed-loop governance where a risk signal automatically triggers remediation is where operational speed and scale is experienced.
Do this:
- Automate decisions where the risk is low and the policy is clear (e.g., revoke unused elevated privileges after 60 days).
- Use GenAI and ML to make recommendations more explainable and adaptable.
- Measure the business impact: Fewer manual reviews, faster access times, and cleaner entitlements
Key Takeway: True maturity isn’t just insight. It’s action. AI should lighten the load for your team – not create more dashboards. Work with your vendors to measure outcomes delivered by AI and automation. Ensure your agentic AI can continue learning to keep up with your dynamic environment.
Final Thoughts: Agentic AI That Works for You, With You
Access governance doesn’t need more hype. It needs help. You don’t have to wait - you can deploy it today.
With the right foundation, the right model maturity, and the right controls, AI and agentic AI can transform IGA from reactive to autonomous – without sacrificing transparency or trust.
Let AI do what it does best: assess your environment, recommend decisions, surface anomalies, and act with precision. And have your team focus what they do best: oversee the policies, act with confidence, and lead the future of secure access.
Want to see what AI-powered access administration looks like in action? Request a demo or explore how Lumos delivers Autonomous Identity.
















